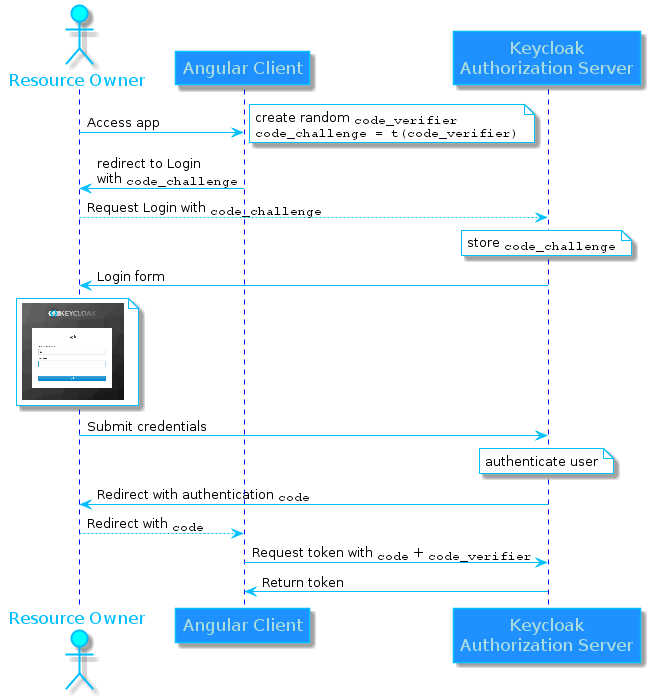
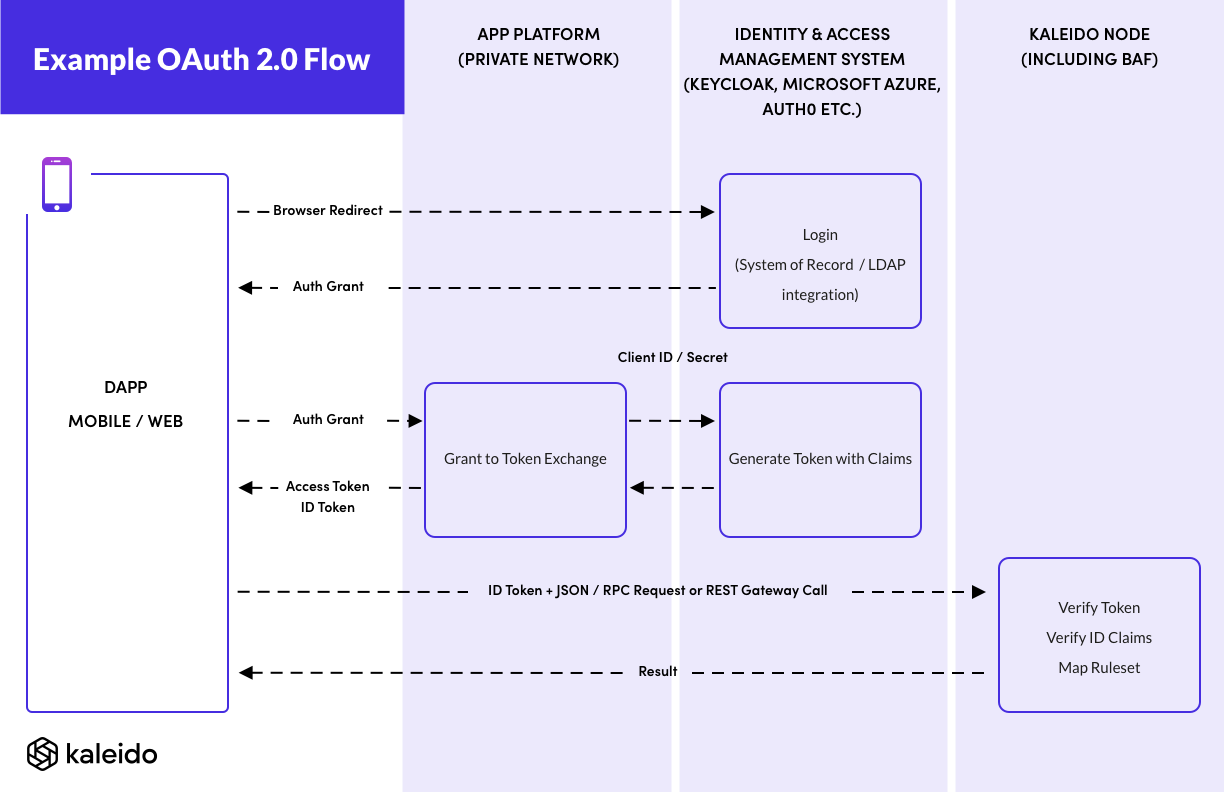
Securing Web Applications With Keycloak Using OAuth 2.0 Authorization Code Flow and PKCE - Jeroen Meys — Ordina JWorks Tech Blog

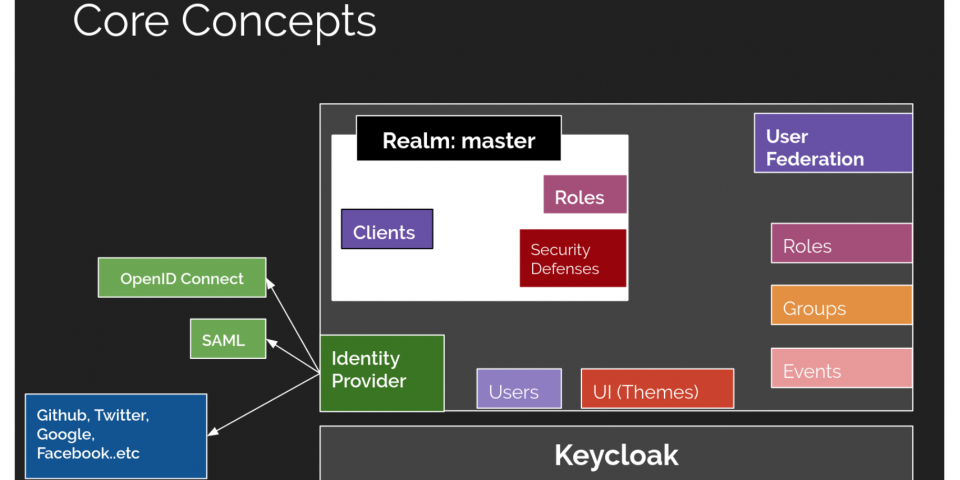
Introduction to Keycloak. Keycloak is an open-source identity and… | by Abdulsamet İLERİ | CodeX | Medium
Introduction to Building an Effective Identity and Access Management Architecture with Keycloak | by Santosh Shinde | Medium